How to Turn On Stolen Device Protection Feature on iPhones (And What It Is?)
In recent times, there’s been a surge in incidents where thieves target iPhone users, stealing their devices and accessing sensitive information like bank apps and iCloud accounts.
To counteract this, Apple has introduced the ‘Stolen Device Protection’ feature in its iOS 17.3 update.
This guide aims to provide a clear and straightforward overview of how to use this feature to enhance the security of your iPhone.
What is Stolen Device Protection ?
Apple’s ‘Stolen Device Protection’ is a proactive security measure, developed in response to the increasing trend of iPhone thefts.
This feature is carefully designed to protect your personal information and stop people who shouldn’t get into your accounts, especially when you’re using your device somewhere different, like not at home or work.
It requires you to use Face ID to access important settings and personal information.
This move ensures that only the legitimate owner can operate sensitive functions of the device.
Moreover, there’s the inclusion of the ‘Security Delay Protocol’ feature.
This innovative feature introduces a strategic delay, especially crucial when the device is in the hands of an unauthorized person.
Actions that bear significant impact, like altering Apple ID settings or deactivating certain security features, are subjected to an hour-long waiting period.
This delay acts as a critical window, allowing you the opportunity to secure your device and account.
How to Turn On Stolen Device Protection
Before you can use ‘Stolen Device Protection’, make sure your iPhone is running the latest iOS version, which is iOS 17.3.
This version includes the new security feature.
To check your iOS version, go to ‘Settings‘, then ‘General‘, and tap on ‘Software Update‘.
If an update is available, follow the prompts to install it.
Now, here are the steps to turn on the Stolen Device Protection feature:
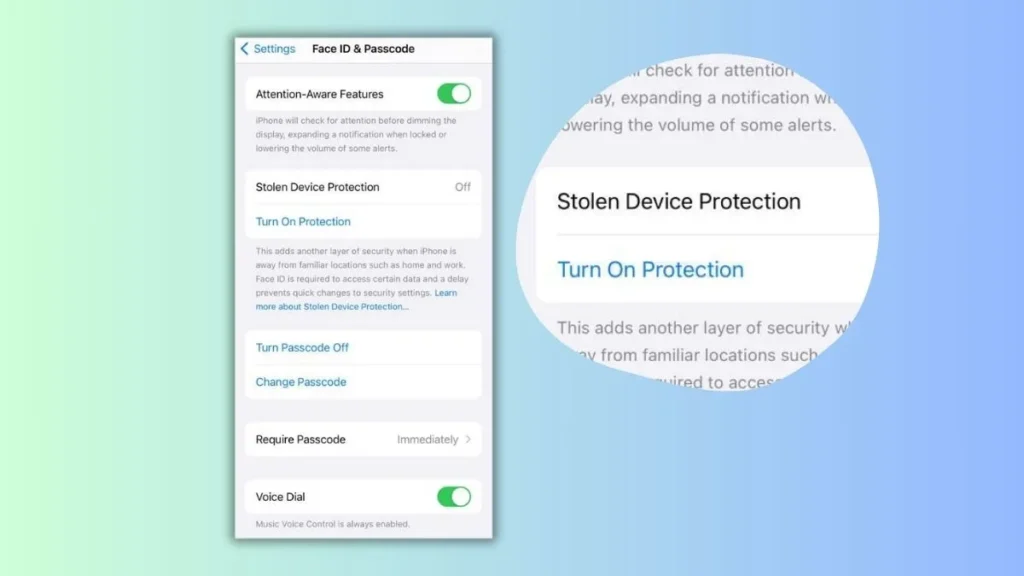
- Once your iPhone is updated, open the ‘Settings‘ app.
- In ‘Settings‘, look for the option labeled ‘Face ID & Passcode‘.
- You will be prompted to enter your device’s passcode. This is the same code you use to unlock your phone. Enter it to access the next screen.
- After entering your passcode, you will see various settings related to Face ID and your passcode. Scroll through these options until you find ‘Stolen Device Protection‘.
- Under ‘Stolen Device Protection‘, there will be a switch that says ‘Turn on Protection‘. This is what you need to tap to activate the feature.
- Once you tap it, ‘Stolen Device Protection’ will be enabled on your iPhone. You might see a confirmation message or the switch might change color, indicating that the feature is now active.
Here is an image that shows this process:

Key Features
1. Biometric Authentication for Unfamiliar Locations:
- Primary Function: When your iPhone detects that it’s in a location not marked as ‘familiar’ (such as places you don’t frequently visit), it automatically enhances security.
- How It Works: In these situations, for any sensitive action, your iPhone will require Face ID verification. This means that if someone who isn’t you tries to access certain features or settings, they’ll need your biometric data — something only you can provide.
- Impacted Actions: This includes tasks like
- Using passwords or passkeys stored in your Keychain
- Accessing payment methods saved in Safari for autofill
- Turning off Lost Mode
- Erasing everything from your iPhone
- Getting a new Apple Card
- Checking your Apple Card’s virtual number
- Doing certain things with Apple Cash and Savings in your Wallet, like moving money
- Using your iPhone to set up a new device
2. Security Delay Protocol:
- Purpose: This feature introduces a deliberate delay in processing certain critical actions. It’s designed to provide you with extra time to react if your phone is stolen.
- Mechanism: If an attempt is made to change key settings like your Apple ID password, the phone initiates a one-hour delay. During this period, the action is essentially ‘frozen’, preventing immediate unauthorized changes.
- Dual Authentication Requirement: Even after the hour passes, a second round of biometric authentication is required, adding an additional layer of security.
- Strategic Advantage: This delay is crucial, as it hampers a thief’s ability to quickly make changes to your phone, giving you time to locate the device or secure your accounts.
- Impacted Actions: The delay applies to several critical operations, such as
- Turning off ‘Stolen Device Protection’
- Changing your Apple ID password
- Signing out of your Apple ID
- Altering your Apple ID account security settings
- Adding or removing Face ID information
- Changing your iPhone passcode
- Resetting all your iPhone’s settings
- Turning off ‘Find My’
3. Context-Sensitive Operation:
- Intelligent Functionality: ‘Stolen Device Protection’ is smart enough to differentiate between familiar and unfamiliar locations. This means that it won’t impose additional security steps when you’re using your iPhone in known places like your home or office.
- Regular Usage: In familiar settings, your iPhone will function normally, allowing you to use your passcode as you typically would without extra steps.
When to Deactivate Stolen Device Protection:
- Turning Off in Unfamiliar Locations: Attempting to deactivate ‘Stolen Device Protection’ in a location that your iPhone doesn’t recognize will trigger the security delay.
- Important Before Selling/Trading: It’s crucial to remember to turn off this feature before selling or giving away your iPhone to prevent unnecessary complications for the new owner.
What Stolen Device Protection Doesn’t Cover
1. Regular Transactions and Purchases
The ‘Stolen Device Protection’ feature does not interfere with regular transactions like purchases made through Apple Pay.
You can still use your iPhone passcode for these transactions, as the feature does not extend its security protocols to routine financial activities.
While this ensures convenience in everyday use, it also means that if your device is stolen, the thief could potentially make purchases using your passcode, provided they have access to it.
2. General Device Operations in Familiar Locations
In locations that your iPhone recognizes as ‘familiar’, such as your home or office, ‘Stolen Device Protection’ does not impose additional security measures.
Your device will operate as it usually does without the enhanced security protocols.
This design choice ensures that your day-to-day interaction with your iPhone remains seamless and user-friendly in known environments.
3. Access to Certain Device Features
The protection mainly focuses on critical changes and sensitive areas like Apple ID settings, biometric data, and significant device settings.
It does not cover all aspects of device usage.
Features like accessing photos, music, non-sensitive apps, and general device settings may not require the heightened security checks imposed by ‘Stolen Device Protection’.
4. Non-Security Related Functions
‘Stolen Device Protection’ is specifically tailored to enhance security against unauthorized access and theft.
It does not extend to improving the iPhone’s functionality in other areas like performance optimization, battery life, or general software issues.
5. Physical Theft Deterrence
The feature does not physically prevent theft.
It is designed to make it harder for thieves to access your information and make unauthorized changes but does not include mechanisms to prevent the physical act of stealing the iPhone itself.
6. Complete Data Protection
While ‘Stolen Device Protection’ significantly enhances security, it is not a comprehensive solution for all data protection needs.
You are still advised to follow general best practices for securing your devices and personal information.
This includes using strong passwords and being cautious about where and how you use your device.
Final Thoughts
‘Stolen Device Protection’ on the iPhone is a robust feature focused on preventing unauthorized access and securing critical settings in the event of theft.
However, it is important for users to be aware of its limitations and understand that it does not cover every aspect of iPhone usage or completely eliminate the risk associated with device theft.
Combining this feature with general good practices in digital security is the best approach for comprehensive protection.